In this article, we are going to know about what is cyber security ? Cyber security refers to the safety and protection of devices , processes, infrastructure and assets of the organizations from cyber attack, data thefts, breaches, unauthorized access and etc . This is the meaning of cyber security. It is also known as computer security.
what is cyber security importance ? Due to to increase in technology, now a days in every field computer and internet are used. In today’s time every work is done through the internet ,whether the work is of the government or any private company. Even the money transactions are done through the internet. So the devices of the users are constantly linked to the internet. That’s why users should be provided with security for their data through Cyber security. Also you can make a great career in cyber security.
With the rise of technology and the increasing inter-linking of organizational systems and networks, effective cyber security management and strategy are necessary for organizations of all sizes and types. Every organization should know about what is cyber security .
What is the cyber ?
what is the cyber : Cyber is related to, or involve computers or computer networks(such as the Internet). In this article we are going to learn about how to provide security to the cyber. That is known as cyber security.
What cyber attack ?
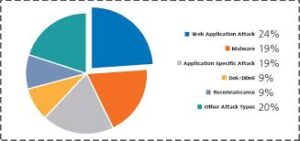
The meaning of cyber attack is just as pollution was a side effect of the Industrial Revolution, so are the many security vulnerabilities that comes with the increased Internet connectivity. Cyber attacks are exploitations of these vulnerabilities for the foremost part. Individuals and businesses have found ways to counter what cyber attack employing a sort ofsafety and protection measures and just good old common sense. Cyber attack is threat in computer security.
What are cyber threats ?
Following are the threat in cyber security :
What is network security threat ?
Do you know what is network security threat ?
A network security threat is an effort to obtain illegal admission to your organization’s network, to take your data without your knowledge, or execute other malicious pursuits. Your network security is at risk or vulnerable if or when there is a weakness or vulnerability within your computer network.
(1) Malware attack:
Trojan adware and spyware are few malware attacks. If you download any suspicious attachments online then your system might can get computed by certain malicious viruses embedded within the attachments.
(2) Phishing attack:
Here the hacker usually sends fraudulent emails which appear to be coming from a legitimate source. This is done to install Malware or to Steel sensitive data like credit card information and login credentials.
(3) Man in the middle attack:-
Here the hackers get access to the information Path between your device and the websites server. The hacker’s computer takes an IP address. By doing so, the communication line between you and the website is secretly intercepted. This commonly happens with unsecured Wi-Fi networks and also through Malware.
(4) Password attacks:
This is one of the easiest way to hack system. Here your password can be created by using either common password or trying every possible alphabetical combination.
Lets have a look at a few of the cyber attacks that companies are subjected to.
- Advanced persistent threat Apt:-
Various Public Sector Organizations and Private Large corporations face the advanced persistent threat Apt. In this form of attack hackers gain access to networks for long period in order to continuously gain confidential information.
- Denial of services:-
Companies also witnessed denial of service attack. Where network are flooded with traffic which successively leaves legitimate service requests.
- Distributed denial of services:-
A DDOS attack is when multiple systems are used to launch the attack. When a hacker manipulates a standard SQL query in a database-driven Website. It is known as SQL injection attack. By doing so hackers can view, edit and delete tables from databases amidst a plethora of Cyber attacks.
That’s why every organization should know about what is cyber security.
What is CIA in cyber security ?

what is CIA in cyber security : The CIA Triad is actually a security model that has been developed to help people think about various parts of IT security.
Confidentiality
It’s crucial in today’s world for people to protect their sensitive, private information from unauthorized access.
Protecting confidentiality is dependent on being able to define and enforce certain access levels for information. That’s why every organization should know about what is cyber security.
Integrity
Data integrity is what the “I” in CIA Triad stands for. This is an essential component of the CIA Triad and designed to protect data from deletion or modification by any unauthorized party.
Availability
This is the final component of the CIA Triad and refers to the actual availability of your data. Authentication mechanisms, access channels, and systems all have to work properly for the information they protect and ensure it’s available when it is needed.
What are the different types of cyber security ?
What are cyber security types ?
Application security
This type of computer security includes the measure and counter measures meant to tackle the threats and vulnerabilities that arise in the development stage of an application. Such as design application, development, deployment, maintenance upgrade, etc.(some of the techniques used includes input parameter validation, session management, user authentication, and authorization, etc)
What is an information security ?
This type of computer security refers to the safety and protection of information and data from theft, unauthorized access, breaches , etc in order to uphold user privacy and prevent identity theft.
Disaster recovery
This type of computer security involves planning and strategizing to enable organizations to recover from IT disasters. This includes risk assessment analysis, privatizing, and establish disaster response and recovery mechanisms in place. This enables organizations to recover faster from disasters and minimize losses.
Network security
This type of computer security constitutes monitoring and preventing authorized access and exploitation of the internal network of an organization, by leveraging both hardware and software technologies.
Network security ensures that internal networks are safe, reliable, and usable. Antivirus and anti-software, VPN, IPS, firewall, etc. are used to prevent cyber threats facing the organization.
Website security
This type of computer security is used to prevent and protect websites from risk on the internet. The Holistic website security programs will cover the website database, applications, source code, and files. There has been a steady rise in the number of data breaches on websites in the past few years. Resulting in identity thefts, downtime, financial losses, loss of reputation and brand image, etc.
The main reason for this has been the misconception among website owners that their website is protected by a website hosting provider, thus leaving them vulnerable to thefts.
Endpoint security
This type of computer security enables organizations to protect their server, workstations, and mobile devices from remote and local attacks. Since devices on a network are interconnected, it creates an entry point for threats and vulnerabilities. Endpoint security effectively secures the network by blocking attempts made to accept this entry point.
What is hacking in cyber security ?
Ethical hacking involves an authorized attempt to gain unauthorized access to a computer system, application, or data. Carrying out an ethical hack involves duplicating strategies and actions of malicious attackers.
What is a framework in cybersecurity ?
What is cyber security frameworks :
- Computer security protects data and networks from any virtual and digital unauthorized access.
- Improvement in information security management and business continuity.
- Providing security consolidation to stakeholders in terms of your information security arrangements.
- Enhancing security controls without compromising company credentials.
- Preemptive to a potential cyberattack and recovery protocols for a quick revival.
What is the importance of cyber security ?
There are roughly 4,000 cyberattacks every day. One reason the rate of cybercrime continues to rise is because it is cheap, fast, and highly profitable compared to other types of crime. This is why that’s where cybercriminals are headed. Cybercrime can cost organizations millions of dollars in damage. But it’s not just about financial costs. Cyber attacks also can damage their reputations, their ability to try business and sometimes even compromise the physical safety and health of employees, patients, customers, etc.
What is the need of cyber security ?
When people do not feel that their information is being properly secured and kept private, they start to lose trust within the brand. the merchandise and therefore the services. User identities now protect billions of point. This is data that we’re transmitting at work, data from internet-of-things devices like a coffee maker or the printers we use, and our personal information as more of our data is becoming digitized. Securing these identities helps reduce the danger of cybercrime to organizations and to individuals.
As organizations evolve, merge, and grow over time their networks and systems naturally get more complicated and things may slip through the cracks. Additionally, end-users like you and me can often be the weakest link in an organization’s security. And that requires the organization to put robust security and compliance protection in place. We should all care about cybersecurity. It’s a part of all of our jobs because it’s an important part of every organization. And when properly implemented, a correct security approach can help us. That’s why every organization should know about what is cyber security.
FAQs :
1)What is cyber security in simple words ?
Cyber security is the protection of networks, technology, computer, and assets from digital data thefts and unauthorized access through the internet. This is the meaning of cyber security. It is also known as computer security.
2)What is cyber security threat ?
Cyber security threats :
- Malware
- Emotet
- Denial of Service
- Man in the Middle
- Phishing
- SQL Injection
- Password Attacks
3)Who is most at risk for cyber attacks?
5 Industries who should have proper knowledge about what is cyber security
- Small businesses.
- Healthcare institutions.
- Government agencies.
- Energy companies.
- Higher education facilities
4)Which country has the best cyber security ?
What is cyber security best country :
- Russia
- Canada
- The United Kingdom.
- Malaysia
- China
- France
- Sweden
- Estonia
5) What are cyber security 4 types ?
- Network security. Network security is used to prevent unauthorized or malicious users from getting inside your network.
- Internet security.
- Endpoint security.
- Cloud security.
- Application security.
6) What are the examples of cyber attack?
What is cyber security faced attacks :
- Malware is a term used to describe malicious software, including spyware, ransomware, viruses, and worms.
- Phishing.
- Man-in-the-middle attack.
- Denial-of-service attack.
- SQL injection.
- Zero-day exploit.
- DNS Tunneling.
7) What is cyber security required skills ?
The Top Skills Required for Cybersecurity Jobs
- Problem-Solving Skills.
- Technical Aptitude.
- Knowledge of Security Across Various Platforms.
- Attention to Detail.
- Communication Skills.
- Fundamental Computer Forensics Skills.
- A Desire to Learn.
- An Understanding of Hacking.
8)What are cyber security pillars ?
The CIA triad refers to an information security model made up of the three main components:
- Confidentiality
- Integrity
- Availability
Each component represents a fundamental objective of information security.
9) Does cybersecurity need math?
Cyber security requires strong math background. You should have skills in analytics and statistical analysis. In addition to a degree program, computer security specialists should also be part of a number of Certification programs.
10) How many cyber attacks happened in 2020?
There were in total 1001 cases of cyber attacks in the United States of America in the year 2020. Around 158 million individuals were affected by those attacks.
11) Can I learn what is cyber security on my own?
Yes, you can definitely self-learn cyber security. There are numerous online sources available nowadays, with the help of which you can learn computer security at your home.
12) What is cyber security difficulty level ?
Cyber security degrees are more challenging than the other kind of non-tech degrees. You need to be hardworking and passionate about computer security and the virtual or digital world for achieving your educational qualifications.
13) What is cyber security faced attacks harmfulness level?
Cyber attacks can cause:
- Electrical blackouts
- Failure of military equipment
- Breaches of national security secrets digitally.
- Theft of valuable, sensitive data.
- Disrupt phone and computer networks.
- Paralyze systems.
15) What are cyber security five pillars ?
The Five Pillars of Information Assurance model includes :
- Confidentiality
- Integrity.
- Availability.
- Authenticity.
- Non-repudiation of user data.


